Major Bug in Trend Micro OfficeScan 8.0
Problem Description:-
There is a major bug in Trend Micro OfficeScan 8.0
The client will keep on sending quanrantine file in C:\Program Files\Trend Micro\OfficeScan Client\SUSPECT folder to the Trend Micro OfficeScan 8.0 Server.
It impact Trend Micro OfficeScan 8.0 with Service Pack 1 (Shown below is the component version of the impacted machine.
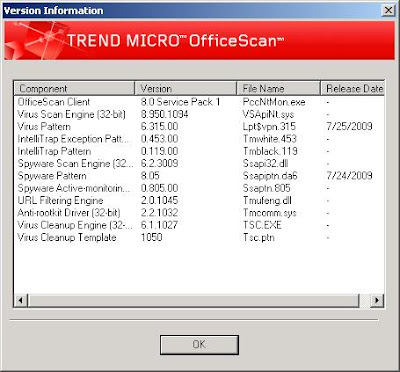
Damage ? :-
The damange is so massive and u can call this an internal major DDOS attack.
Root cause?
Unknown. Some trend engineer claim it is due to the scan engine 8.950.1094 and some claim it is due to the folder permission is correct.
Solution?
There is no real solution at the moment.
But you ease the damage by doing the following task.
a) rename the cgirecvfile.exe on the OfficeScan server (\pccsrv\web_osce\web\cgi) to prevent high CPU usage on the OSCE server.
b) change virus clean action from IntelliAction to Clean or Delete..(the idea here is not to choose the quarantine as part of the clean action item)
Well u might have thought the action above will solve the issue will ya? Well u r wrong!!!
The client will still continue sending nonsense to the server cause the C:\Program Files\Trend Micro\OfficeScan Client\SUSPECT folder is not empty yet. It might not be able to establish a connection but will still continue to ping the server.
u might want to write a script which stop the ntrtscan and tmlisten and then del all content in C:\Program Files\Trend Micro\OfficeScan Client\SUSPECT
:)
Well by doing all this u r protected from your internal menace from the time being..
Conclusion:-
Stay away from scan engine 8.950 the quality of trend micro product is really going from bad to worst..god i hate this...
LATEST UPDATE!!!
Ok this bug is mainly due to these 2 folder permission change mysteriously:-
C:\Program Files\Trend Micro\OfficeScan Client\FLog
C:\Program Files\Trend Micro\OfficeScan Client\Suspect
To fix it u need to grant full permission to everyone on the two folder above..
u can either script it or do it manually...cheers.
or Trend Micro did recommend this:- change the security from normal to high back to normal.
Mission Accomplish.
There is a major bug in Trend Micro OfficeScan 8.0
The client will keep on sending quanrantine file in C:\Program Files\Trend Micro\OfficeScan Client\SUSPECT folder to the Trend Micro OfficeScan 8.0 Server.
It impact Trend Micro OfficeScan 8.0 with Service Pack 1 (Shown below is the component version of the impacted machine.

Damage ? :-
The damange is so massive and u can call this an internal major DDOS attack.
Root cause?
Unknown. Some trend engineer claim it is due to the scan engine 8.950.1094 and some claim it is due to the folder permission is correct.
Solution?
There is no real solution at the moment.
But you ease the damage by doing the following task.
a) rename the cgirecvfile.exe on the OfficeScan server (\pccsrv\web_osce\web\cgi) to prevent high CPU usage on the OSCE server.
b) change virus clean action from IntelliAction to Clean or Delete..(the idea here is not to choose the quarantine as part of the clean action item)
Well u might have thought the action above will solve the issue will ya? Well u r wrong!!!
The client will still continue sending nonsense to the server cause the C:\Program Files\Trend Micro\OfficeScan Client\SUSPECT folder is not empty yet. It might not be able to establish a connection but will still continue to ping the server.
u might want to write a script which stop the ntrtscan and tmlisten and then del all content in C:\Program Files\Trend Micro\OfficeScan Client\SUSPECT
:)
Well by doing all this u r protected from your internal menace from the time being..
Conclusion:-
Stay away from scan engine 8.950 the quality of trend micro product is really going from bad to worst..god i hate this...
LATEST UPDATE!!!
Ok this bug is mainly due to these 2 folder permission change mysteriously:-
C:\Program Files\Trend Micro\OfficeScan Client\FLog
C:\Program Files\Trend Micro\OfficeScan Client\Suspect
To fix it u need to grant full permission to everyone on the two folder above..
u can either script it or do it manually...cheers.
or Trend Micro did recommend this:- change the security from normal to high back to normal.
Mission Accomplish.
Comments